 Social media addiction is a problem that plagues most modern businesses. Even though it’s a best practice to leverage social media to your business’s advantage, it’s a well-known fact that social media addiction can lead to wasted time and distractions in the office. In order to beat social media addiction in the office, it’s best to understand how it comes about, and what you can do to help your workers leave it alone, rather than locking everything down completely.
Social media addiction is a problem that plagues most modern businesses. Even though it’s a best practice to leverage social media to your business’s advantage, it’s a well-known fact that social media addiction can lead to wasted time and distractions in the office. In order to beat social media addiction in the office, it’s best to understand how it comes about, and what you can do to help your workers leave it alone, rather than locking everything down completely.
For example, there was a recent study that takes a close look at Facebook, which is largely considered the most-used social media outlet on the market. Why can’t people leave their Facebook alone, even at work? The study, performed by Cornell University researchers, is based on the online experiment called 99 Days of Freedom, in which participants attempt to go 99 days without checking Facebook. How’s that for a challenge?
Additionally, users were prompted to take surveys at the 33, 66, and 99-day milestones, which go into detail about how and why they felt pulled toward Facebook. These surveys were designed by Just. Researchers at Leiden University. See some of the results for yourself here:
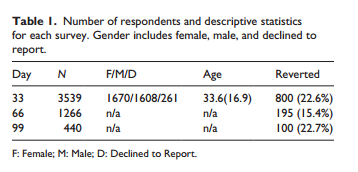
As it turns out, more people are capable of resisting the calls of Facebook than you might think. There was a significant number of users who were capable of going 99 days without Facebook, and only a relatively small number of users went back to Facebook. The following are trends that led users to return to Facebook, prior to the ending of the 99-day period.
- Self-diagnosed addiction: Just like any other addiction, people who feel Facebook is addicting will naturally be drawn to it, making it more difficult to give up. This is generally the case if users make a habit or routine out of checking their Facebook.
- Privacy: If users suspect that their Facebook activity is monitored, they’re less likely to return to it. Considering how many workplaces monitor their employees’ Internet activity, this shouldn’t come as a surprise. People want privacy, but if they want to maximize their web privacy, they won’t be using Facebook at all. The privacy element helps to keep users off of Facebook at the office, but fear-mongering doesn’t help anyone, so proceed with caution.
- Mood: A user’s mood can affect how often, and when, they might check their social media. This might seem a bit strange at first, but it makes sense. If a user is engaged and entertained, they’ll be less tempted to engage in social media. On the flip side, if they’re bored and disengaged, they’ll be more likely to turn to Facebook.
- Other Social Media: Users who have more than one social media account, like Twitter or Instagram, are less drawn to Facebook. This is probably due to users having somewhere else to go to satiate their hunger for social media.
Over the course of the 99 days, users who were able to give up Facebook saved an average of 28 hours. That’s over one whole day, or over three eight-hour work shifts that could be better used for other initiatives. Even if social media is something that’s bad in large quantities, most enjoyable things in life are; thus, it’s important to remember that every good thing should be taken in moderation. Limiting your exposure to social media essentially comes down to practicing self-control.
This is why it’s not always a good thing to block social media from your company’s workstations. A better route would be to approach blocking social media the same way you handle managing it in your own life: with moderation. Rather than blocking social media for all employees, only do so with problem employees that waste their days away on Facebook. This way, social media can be exploited by those who need it to perform their daily duties, while problem employees aren’t allowed to access it. Remember, using social media should be considered a privilege, one that can be revoked if it’s abused.
What we recommend is using a web content blocking solution that allows administrators to filter web content on a per-user basis. This way, you can help employees rehabilitate their bad habits, without lowering morale for the employees who do their jobs properly.
For more information about how our web content blocking solution can help your team beat social media addiction, give Voyage Technology a call at 800.618.9844.


