 As great as Gmail is, sometimes, you might have difficulty locating certain messages, especially if they were sent months, or even years ago. If you happen to misplace a message, you can use the search feature to locate it.
As great as Gmail is, sometimes, you might have difficulty locating certain messages, especially if they were sent months, or even years ago. If you happen to misplace a message, you can use the search feature to locate it.
Performing a search in Gmail is as simple as using the search bar at the top of the screen, just above the inbox. You can use this search feature for a basic inbox search, but there are options that allow for more comprehensive searches. Here are three steps that you can take to perform better Gmail searches for your missing or desired messages.
First, enter your search results in the search bar. If you don’t find your desired messages, click the down arrow:
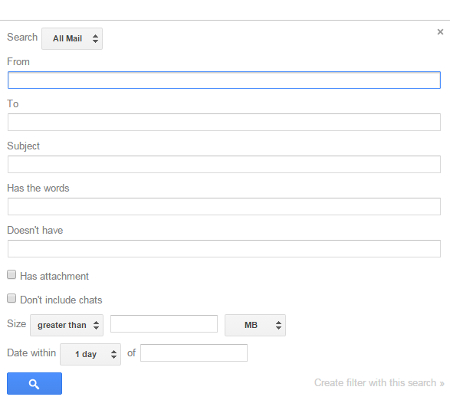
A window will pop up that allows you to sort through your messages according to certain criteria, like sender, receiver, subject, keywords, etc. You can also omit certain results by taking advantage of the “Doesn’t have,” field. Use these checkboxes to determine whether or not the messages have attachments, or you can apply a range for size or date to help you narrow down the search results.
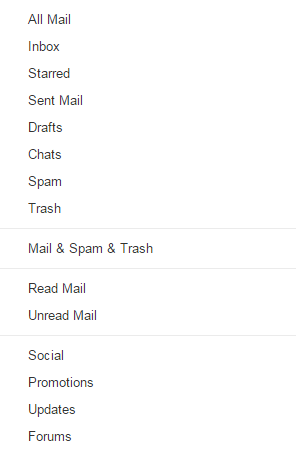
One of the most notable features of Gmail’s search function is the top button that defaults to “All Mail.” By clicking it, you’ll be provided several options that you can use to search through specific parts of your Gmail account, including inbox, sent messages, spam, and trash. This helps to make sure that you don’t miss messages in the future.
If there are messages in your spam or trash that match your search, Gmail will display a message underneath your inbox that says, “Some messages in Trash or Spam match your search. View messages.” By clicking the link, you’ll be shown the messages.
These updates to Gmail only apply to the web application at this time, as more comprehensive search functions aren’t currently available on the mobile application. That doesn’t mean they won’t arrive in the near future, though.
For more great tips, be sure to subscribe to Voyage Technology’s blog.


