 Logging into an account only to find out that you’ve been hacked can be a real hassle. If you’re wondering why and how this could have happened, you’re in luck; some accounts, like Google, record when and how the account is accessed, and finding out how is as easy as checking out your security settings. Here’s how you can see who is accessing your account, and how.
Logging into an account only to find out that you’ve been hacked can be a real hassle. If you’re wondering why and how this could have happened, you’re in luck; some accounts, like Google, record when and how the account is accessed, and finding out how is as easy as checking out your security settings. Here’s how you can see who is accessing your account, and how.
The first step is to sign into your Google account. Hopefully, whoever is tampering with your account hasn’t changed your password on you. Click the grid-like icon in the top right corner of the screen that appears right next to your account name. Click on My Account.
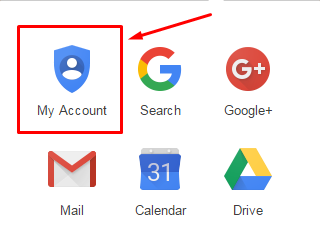
This is the central location of all things related to the settings of your Google account. Click on Sign-in & security.
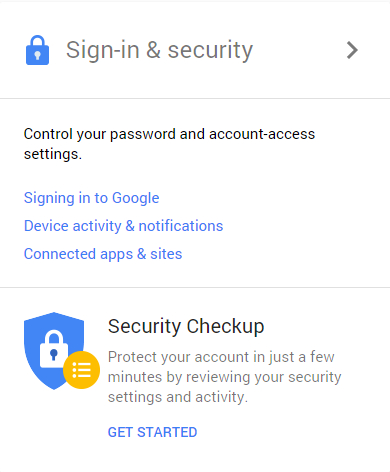
Next, you can scroll down to the Device activity & notifications section, or select it in the table of contents that appears in the left sidebar. This will show you which devices were last used to access your account.
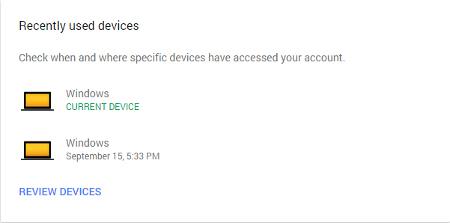
Now, all you have to do is click on Review Devices. This selection shows you what’s going on in your account, including approximate locations for where your account was accessed, the browser they used, and the country. This powerful tool for your Google account security is very simple to use and can effectively help you keep strangers from causing too much trouble.
If you notice that there’s some unsavory activity going on, you should reset your password immediately and set up security notifications that inform you when a hacker or other malicious entity tries to sign into your account. The ability to review devices that are accessing your account gives you the chance to review your account’s security policies and take greater precautions against attacks.
Your Google account also has a ton of other great security features available, with some of the most important ones being two-step verification, recovery options, password resetting, and application settings. Take the time to go through each of these options and optimize your security settings to mitigate the possibility of any future hacking activity.
For more tips on how to keep your online accounts secure, subscribe to Voyage Technology’s blog.


